Statement of Current Operations
Technology Consultant Keung Wong Introduces the Statement of Current Operations
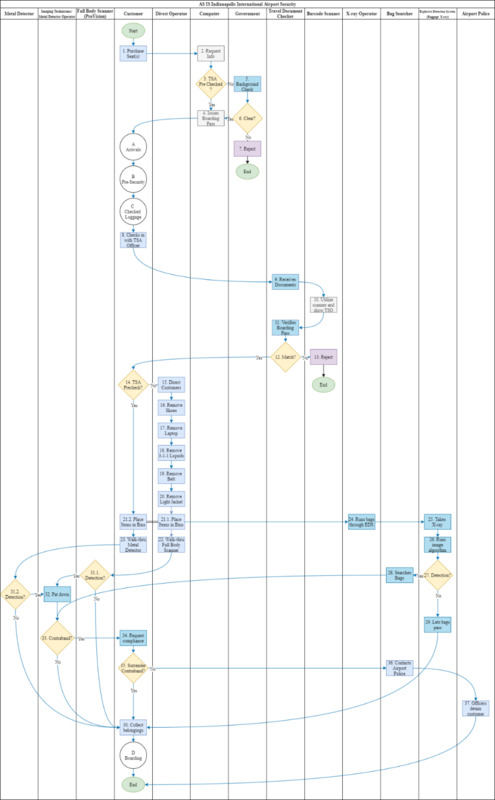
Figure 4: As-Is Security Business Process Diagram
As-Is Security Process
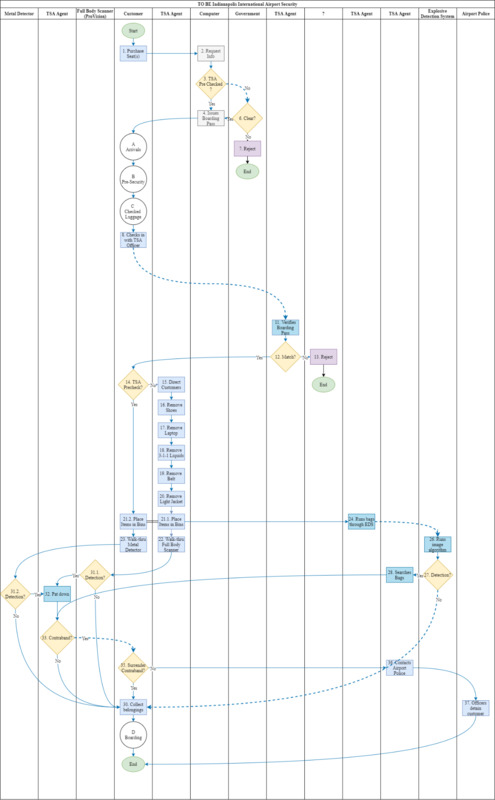
The screening process begins as soon as the purchase of a ticket (1), either via third-party or direct airline access. Information like a person's name, date of birth, and gender is asked, at the time of the transaction, to trigger a background check at the point of confirmation (2). If there is a Known Traveler Number (KTN), the background check is restricted or nullified to proper for party affiliations or memberships such as TSA PreCheck®, CLEAR®, Global Entry®, NEXUS®, and other known or unclassified groups which had foregone the background check (3). Without a KTN, the entire database of known and unknown risks is accessed for information privy to the operation. This information is run through different algorithms to decide the level of risk associated with each passenger. During the payment inquiry, no-flies are rejected, and payment information does not go through. For all others, payments are processed without discrimination. Passengers will receive a flight number and an itinerary (4).
Upon arrival, if a passenger has been flagged for arrest, airport security goes on standby or requests for backup on the date of departure. Please refer to Diagram A: Arrivals. Passengers can printout their boarding pass at the kiosk or request help at the customer service desk. If passengers have check-in luggage, they will prefer the latter. Please refer to Diagram B: Pre-Security and Diagram C: Checked Luggage. Airport security and TSA are different agencies, so TSO do not make any arrests. Around the time of departure, airport security assembles around the escalator and waits for a signal. When passengers attain a boarding pass, airport security is alerted. While the TSO verifies each boarding pass with their proper respective identification, not only do they separate passengers from non-passengers, but they also confirm any flagged passengers. Unknown threats can go through with the rest of the passengers, to be further screened at the security checkpoint.
There are 13 security lanes in total: six at Concourse B and seven at Concourse A. Although TSA PreCheck® lanes are easily convertible with regular lanes and vice-versa, Concourse A checkpoint has appointed the extra lane for it. The minimal staff for a single lane is seven but for two lanes it is ten, which is possible, due to the sharing of equipment. This makes it optimal, to run in even pairs. There is a walkway behind the civic plaza that allows passengers to move freely from Concourse to Concourse if they pass the screening process at either checkpoint. So that any one of them can be shut down in case of emergency. Each lane must include a male and a female pat-down officer for passengers going through any lane on either Concourse (14). Regular passengers have a divest officer that directs them to remove their shoes, laptops, liquids, belts, and jackets (15-20). The divest officer also instructs them to place their items in bins individually (21.1) and pause in the full-body scanner (22). Passengers with TSA PreCheck® or similar membership can place their items in bins without isolation (21.2) and walk through a metal detector (23).
The items placed in bins are scanned by an explosive detection system and critiqued by the operator (24). The operator takes the x-ray images (25) and processes them through an image algorithm (26). If something is suspicious or alerted by the machine (27), a separate person besides the system operator, titled as the bag searcher, inspects the contents (28). If the contents are safe, they move forward. Otherwise, if there are no detections or anomalies, all items move to the end of the conveyor belt (29). The passenger collects their belongings and makes their way to the re-composure area (30).
Since the process creates the most anxiety and TSA know this, the re-composure area is the last key point of security. The re-composure area is an area found at the boundaries of TSA security where one can restore composure or calmness. It is designed especially for that in mind, with lounge-like seating, soothing wall art, colored lighting, and relaxing music. This is the last line of defense for the TSA and the easiest way to find any anomalies they are looking for.
Passengers either pause in a full-body scanner (31.1) or walk through a metal detector (31.2). If there is no detection, they can collect their belongings and pass through the re-composure area (30). If an alarm goes off or the operator detects something, a person other than the imaging technician pats them down (32) to find a root cause (33). If no contraband is found or everything seems normal, the passenger moves forward (30). If contraband is found, either on the person or in their belongings, the TSO asks the passenger to surrender the item(s) or move to the back of the line (34) (35). If they surrender the contraband, they can move forward (30). If they refuse, the TSO contacts the airport police (36), and they give them an ultimatum (37). Compliant passengers collect their belongings, if any, and pass through the re-composure area. Please refer to Diagram D: Boarding. This process is visualized in Figure 4: As-Is Security Business Process Diagram.
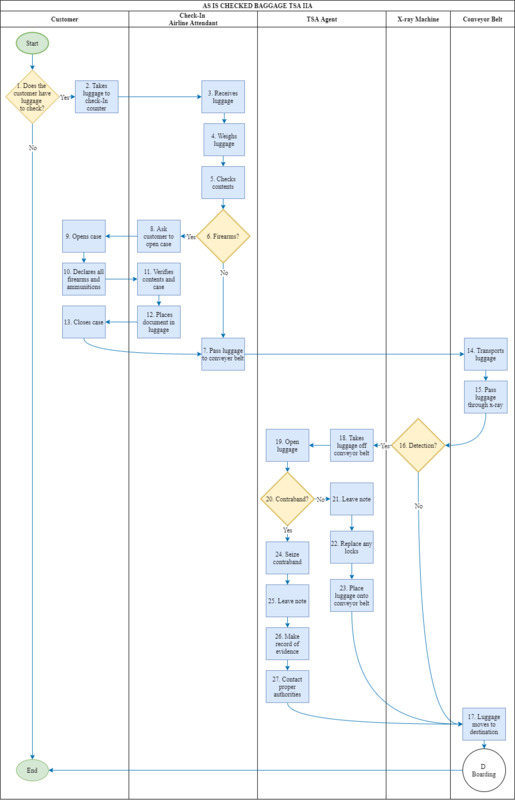
As-Is Checked Baggage
Does the customer have luggage that needs checking (1)? If the customer does not have additional luggage to check, they will exit this process and proceed to check in with a TSA officer. If the customer has extra bags, they will take their bags to the check-in counter (2).
When the attendant receives the bags from the customer (3), they will weigh the bags (4) and check the contents inside each bag (5). The next step for the check-in attendant would be determining whether any bags have registered firearms (6).
If there are no firearms to check, the luggage passes to the conveyor belt (7). If there are firearms, the attendant will ask the customer to open the firearm case (8). Once the customer opens the case (9), they will declare any firearms or ammunition inside of the case (10). After the check-in attendant verifies all the declared firearm and ammunition inside the case (11), the attendant will place certification documentation inside (12), let the customer close the case (13), and pass the luggage to the conveyor belt (7).
Once the luggage is placed onto the conveyor belt, it gets transported to an x-ray system. This system will automatically scan for items that may be contraband (16). If there is no detection from the x-ray, the luggage will pass to its destination (17), at which point the Boarding process will take the luggage, shown in Diagram D: Boarding. If there is a detection by the x-ray, the items get taken off the conveyor belt (18) and opened (19).
TSA agents will then look for what triggered a detection (20). If there is no contraband found, a TSA agent will leave a note inside of the bag (21), replace any locks on the cases (22), and place the luggage back onto the conveyor belt (23). Then the luggage continues to its destination (17). If the TSA finds contraband, they will seize the material (24), leave a note in the luggage (25), make a record of the finding (26), and then contact the proper authorities (27). This process is visualized in Figure 5: As-Is Checked Baggage Diagram.
To-Be Security Process
The screening process begins as soon as a customer books a ticket (1) with the airlines. Information like a person's name, date of birth, and gender is requested (2). The computer system decides whether the customer has TSA PreCheck® (3). If the customer has TSA PreCheck®, a boarding pass is issued (4). TSA PreCheck® customers do not require a background check at the ticket purchase. This is because customers using TSA PreCheck® have undergone a background check, an interview, and submitted fingerprints for record-keeping. Customers without TSA PreCheck® need some type of background check. These algorithms need to determine the level of risk associated with each passenger. If the customer is clear (6), they are issued a boarding pass. Customers who appear on a no-fly list are rejected (7).
Once a customer purchases their ticket, they arrive at the airport on the day of their flight. This is expanded upon in Diagram A: Arrivals. Customers also go through the pre-security process, as shown in Diagram B: Pre-Security. In pre-security, customers drop off their luggage to be screened and boarded, explained in Diagram C: Checked Luggage. After checking their luggage in the pre-security process, the customer checks themselves in with a TSA agent (8). Somehow, the agent needs to verify the authenticity of their boarding pass (11). The agent makes sure that the person on the boarding pass matches the person who is using that document (12). If it is not, the TSA agent rejects the customer (13). If the boarding pass matches, the customer can continue to the security checkpoint lanes.
There are separate lanes for customers going through the normal security process and the TSA PreCheck® process (14). Normal customers have a TSA agent direct them to remove their shoes, laptops, liquids, belts, and jackets (15-20). The agent also instructs them to place their items in a tray (21.1) and walk through the full-body scanner (22). Customers with TSA PreCheck® only place their items in bins (21.2) and walk through a metal detector (23), not a full-body scanner.
Items placed in bins, such as carry-on bags, are put through an explosive detection system by a TSA agent (24). The TSA agent needs to use an Explosive Detection System and process those images through an algorithm (26). If there is a detection (27), the agent inspects the luggage (28). If no detections are made, the customer can collect their belongings (30).
Customers walk through a full-body scanner (31.1) or a metal detector (31.2), depending on if they have TSA PreCheck® or not. If there is no detection, they are sent to collect their belongings (30). If a machine does detect something on the customer, a TSA agent pats down (32) the customer to search for contraband (33). If no contraband is found, the customer continues to collect their belongings (30). If contraband is found either on the person or in their bag, the customer is given a choice (35). If they surrender the contraband, they can collect the rest of their belongings (30). If they refuse, the TSO contacts the airport police (36), who detains the customer (37). After compliant customers collect their belongings, the security process ends. They continue to the boarding process, shown in Diagram D: Boarding. This process is visualized in Figure 6: To-Be Security Process Diagram.
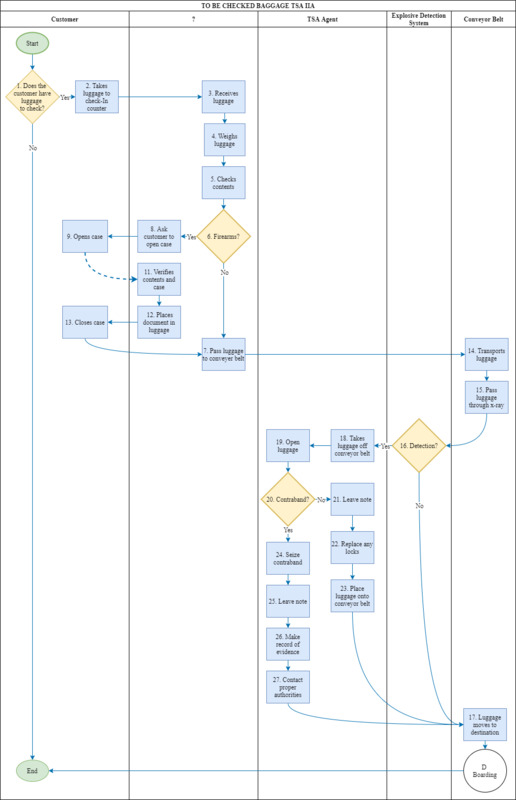
To-Be Checked Baggage
Does the customer have luggage that needs checking (1)? If the customer does not have additional luggage to check, they will exit this process and proceed to check in with a TSA officer. If the customer has extra bags, they will take their bags to the check-in counter (2).
Something or someone receives the bags from the customer (3), that will weigh the bags (4) and check the contents inside each bag (5). The next step is to determine whether any bags have registered firearms (6).
If there are no firearms to check, the luggage passes to the conveyor belt (7). If there are firearms, the customer will be asked to open the firearm case (8). Once the customer opens the case (9), something or someone will verify all firearm and ammunition inside the case (11), place certification documentation inside (12), let the customer close the case (13), and pass the luggage to the conveyor belt (7).
Once the luggage is placed onto the conveyor belt, it gets transported to an explosive detection system. This system will automatically scan for items that may be contraband (16). If there is no detection from the system, the luggage will pass to its destination (17), at which point the boarding process will take the luggage, shown in Diagram D: Boarding. If there is a detection by the system, the items get taken off the conveyor belt (18) and opened (19).
TSA agents will then look for what triggered a detection (20). If there is no contraband found, a TSA agent will leave a note inside of the bag (21), replace any locks on the cases (22), and place the luggage back onto the conveyor belt (23). Then the luggage continues to its destination (17). If the TSA finds contraband, they will seize the material (24), leave a note in the luggage (25), make a record of the finding (26), and then contact the proper authorities (27). This process is visualized in Figure 7: To-Be Checked Baggage Diagram.